Help build a world where passion + purpose thrive.
Cyber Secure Software Engineering
From MVPs to full-stack, mission-critical platforms — we engineer software systems that don’t just work; they lead. Built by elite developers, hardened by security engineers, and optimized for real-world scale.
“Any sufficiently advanced technology is indistinguishable from magic.” – Arthur C. Clarke

🔐 Secure by Design
Cybersecurity isn't a feature. It's the foundation. Our development process bakes in security from day one — with code reviews, threat modeling, zero trust architecture, and secure SDLC practices at every step.
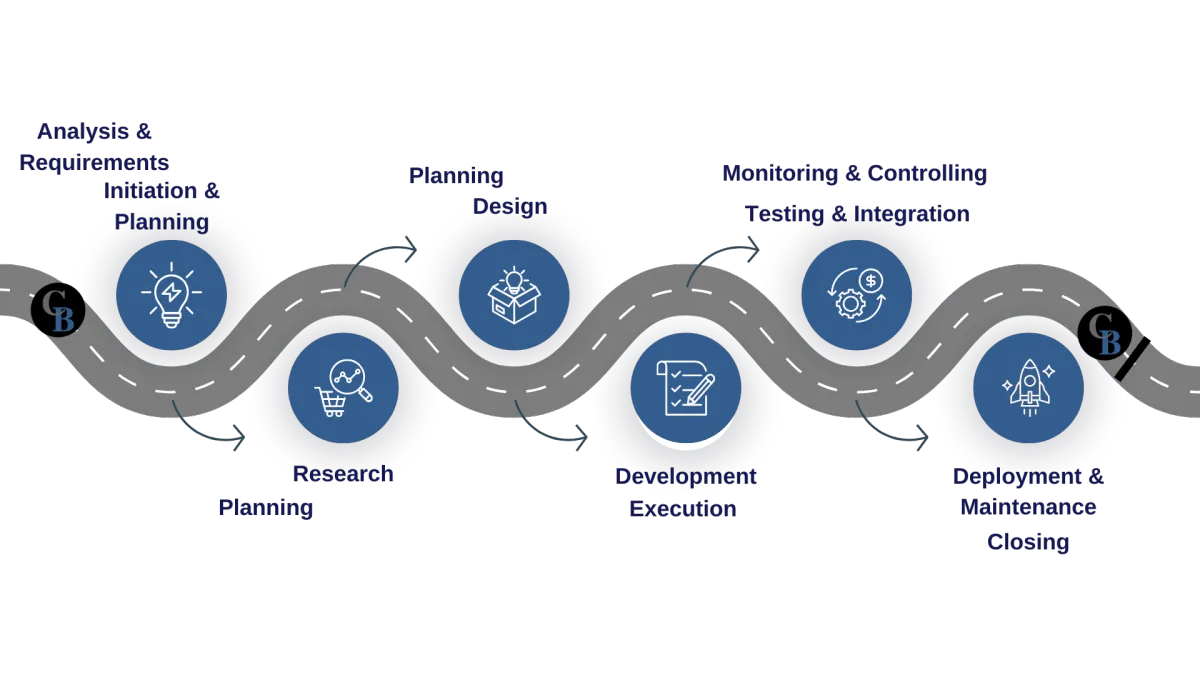
🔐 Explore Our Cyber Secure Software Engineering Capabilities
Code with Confidence. Launch with Purpose.

Secure Software Architecture
Build it Right. Scale it Safe.
CyberBlueprints, Inc. architects secure-by-design systems from the ground up — whether you’re building SaaS, internal apps, or embedded platforms. Our frameworks are built for compliance, resilience, and real-world performance from day one.


MVP to Mission-Critical Platforms
From Idea to Deployment — Without the Guesswork.
Startups, scale-ups, and governments alike rely on us to build the backend of their future. From zero to production, we deliver apps with clean architecture, airtight security, and bulletproof documentation — ready for users, clients, or combat.
DevSecOps & CI/CD Pipelines
Security Baked In. Speed Turned On.
We implement robust DevSecOps pipelines that empower your dev teams to ship fast without breaking things. Integrated testing, compliance automation, and zero-trust builds — all handled.

Secure API & Integration Development
Connect Without Compromise.
Modern software is modular. We engineer and secure the APIs and microservices that connect your systems — and protect them from abuse, leakage, and insider threat.
Application Hardening & Compliance
Built for the Most Regulated Industries.
Whether it’s HIPAA, NIST, GDPR, CMMC FedRAMP,
PCI, or ISO — we get your stack certified and secure. We help you achieve compliance without killing your velocity.


AI/ML Software Integration
Intelligence That Works. Not Just Buzzwords.
We build secure, explainable AI solutions you can trust — for real-time decision engines, adaptive systems, and operational intelligence. Edge-deployed or cloud-native, we keep your models tight and secure.
Legacy System Rebuilds
Old Code? No Problem. We Fix the Past to Secure the Future.
We modernize, refactor, and replatform legacy systems into high-performance, secure, and maintainable codebases. No spaghetti left behind.

Testimonials

Jasmine Richards

We were hacked twice before CyberBlueprints came in. Now? Zero breaches, faster product releases, and total confidence in our software security. These guys don’t just code — they fortify.

Monica Chandler

Our entire app was running on duct tape and prayer. CyberBlueprints rebuilt everything — secure architecture, CI/CD, compliance-ready. Saved us from a nightmare launch and gave us real velocity.

Thomas Krazinski

I’ve worked with dev teams across three continents. Nobody blends security, software engineering, and actual business strategy like CyberBlueprints. They’re our go-to for mission-critical code.
"We make the magic real — and secure." - EL Cruz, Founder
🧬 Cyber Secure Software Engineering – Quick FAQs
❓What makes your software development “cyber secure”?
Every line of code is built with security-first architecture, not just features. We implement threat modeling, zero-trust design principles, and secure-by-default development from day one — so you're not patching holes later. No zero days.
❓Do you work with startups or only large organizations?
Both. We build for mission-critical scale, but we love helping startups bring secure ideas to life. Whether it’s your MVP or your millionth user — we’ve got you.
❓Can you take over an existing insecure codebase?
Yes. We specialize in rescue missions. We'll assess your current stack, fix vulnerabilities, and rebuild what’s broken — fast, lean, and secure.
❓Do you support compliance standards like HIPAA, GDPR, or CMMC?
Absolutely. Our engineers bake in compliance with every build. We make sure your product aligns with the security frameworks your business depends on.
❓Do I need a technical background to work with you?
Nope. Just bring your vision. We’ll translate the tech for you, handle the architecture, security, and code — and keep you in the loop without the jargon.
❓How long does a typical software project take?
Depends on the mission. MVPs can ship in weeks. Complex systems with integrations, AI, or advanced security layers may take months — but we move fast without cutting corners.
❓ Do you work internationally?
Yes. We support Ministries of Technology, NGOs, startups, and sovereign leaders worldwide with strategic cyber engineering solutions.
❓What is OWASP, and why do you follow it?
OWASP (Open Worldwide Application Security Project) is the global gold standard for secure software development. It provides the best practices, testing guides, and frameworks we follow when building apps for web, mobile, critical infrastructure, robotics, and more.
At CyberBlueprints, we don’t just reference OWASP — we live it. Every line of code is checked against the OWASP Top 10 and ASVS (Application Security Verification Standard).
But we take it even further…
We use a battle-tested mix of:
Static Analysis (SAST) – to catch bugs before runtime
Dynamic Analysis (DAST) – to find real-world attack paths
Reverse Engineering – to hunt weaknesses and validate binaries
Fuzz Testing – to simulate chaos and discover zero-days before anyone else
Whether it’s a healthcare app, drone control system, or smart city sensor network — we code like attackers are already inside.
100% nonprofit. No pressure. Just clarity, strategy, and results.
“Creativity is just connecting things.” – Steve Jobs
Portfolio
We Built Cyber Solutions Trusted by $140M+ Firms and U.S. Government Agencies.
🔒 Trusted to Execute. Not Just Advise.
We didn’t “consult.” We built the solutions that cyber firms and U.S. agencies still use today. From the ground up, we designed and implemented scalable cyber operations for elite agencies, top-tier security vendors, and mission-critical organizations — with real-world consequences on the line.
If our frameworks worked for $140M+ security firms and U.S. government agencies... they’ll work for your business, too.
We’ve helped secure everything from
national infrastructure to private enterprises, including:
Government agencies & military units.
High-growth commercial businesses.
Critical infrastructure: energy, finance, healthcare, transportation.
High-net-worth individuals, VIPs, and leadership teams.
Schools, universities, and mission-based organizations.
Whether you're defending a nation, scaling a company, or protecting a personal legacy — we deliver tailored security blueprints that scale with you..











Cyber Engineering
Imagine. Engineer. Impact.

Cyber Security
CPR. Coaching. Command.

Cyber Coaching
Innovate. Secure. Lead.


FOLLOW US AROUND THE WEB

COMPANY
MORE INFO
LEGAL
Copyright 2026. CyberBlueprints.com, Inc. . All Rights Reserved.
CyberBlueprints.com, Inc. is an independent entity operating under the umbrella of The Phoenix Project, Inc., a registered 501(c)(3) nonprofit organization. Profits generated support the charitable mission and programs of The Phoenix Project.
We link to external websites for informational purposes only but do not endorse or guarantee their accuracy. Once you leave our site, you will be subject to the new website’s privacy policy.
This site is not a part of the YouTube, Bing, Google, or Facebook website; Google Inc., Microsoft Inc., or Meta Inc. Additionally, this site is NOT endorsed by YouTube, Google, Bing, or Facebook in any way. FACEBOOK is a trademark of FACEBOOK, Inc. YOUTUBE is a trademark of GOOGLE Inc. BING is a trademark of MICROSOFT Inc.

Youtube
Website